What is an SSH Key?
An SSH key is an alternative to usernames and passwords as a method of user authentication. It is primarily used by presenting an encrypted file to the service instead of a text-based password.
Access credentials for SSH keys are exchanged in the Secure Shell protocol, a secure alternative for the unencrypted Telnet. SSH keys use cryptographic techniques to ensure that all communication to and from the remote server happens in an encrypted manner.
It provides a mechanism for authenticating a remote user, transferring inputs from the client to the host, and relaying the output back to the client.
In practice, each user generates their own SSH key pair, keeping the private half on their machine and installing the public half on servers in which they need access.
An example of how this process works can be demonstrated here:
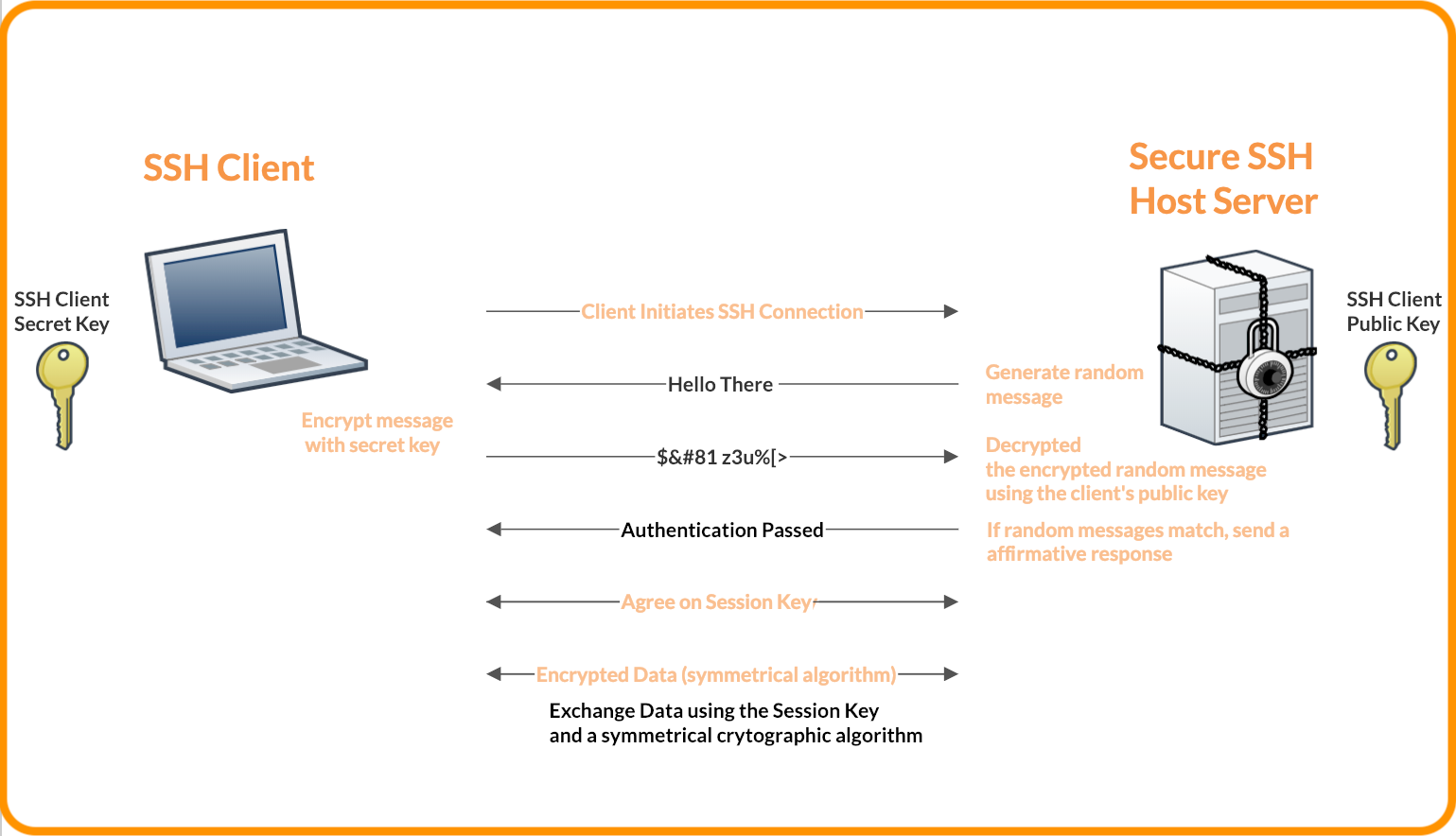
How are SSH Keys Used?
The main use of SSH keys is to log into Linux servers. These servers work behind the scenes to power most websites and apps.
Software engineers need to continually log into these servers to deploy code, fix bugs, and configure settings.
A Manual SSH Key Management Alternative is Foxpass
Foxpass offers the easiest and most secure way to manage your SSH keys and keep your servers secure.
This is just one of the many ways Foxpass offers enterprise-grade security at a more approachable price.


.png)

